Understanding Content Security Policy (CSP) and Sub-resource Integrity (SRI)
At Volusion, we�re committed to keeping your online store secure and your customers safe. Two important security tools we have released to protect your website are Content Security Policy (CSP) and Sub-resource Integrity (SRI). These mechanisms help safeguard your site from common web threats, ensuring a safer browsing experience for your customers. Here�s a simple overview of what they are and how they work.
What is Content Security Policy (CSP)?
Content Security Policy (CSP) is a security feature built into web browsers that helps prevent malicious code from running on your website. It acts like a set of rules that tells the browser what content is safe to load and execute, reducing the risk of attacks like cross-site scripting (XSS)�where hackers inject harmful scripts into your site to steal customer data or redirect users to malicious pages.
How CSP Works
With CSP, we define a policy that specifies:
-
Trusted Sources: Only scripts, images, styles, and other resources from approved sources (e.g., your own domain or trusted third-party providers) can load.
-
Blocked Actions: Untrusted or potentially dangerous content�like inline scripts or scripts from unknown domains�is blocked by the browser.
-
Reporting: If something violates the policy, the browser can report it to us, helping us identify and fix potential vulnerabilities.
For example, if a hacker tries to inject a malicious script into your store�s checkout page, CSP can block it because the script isn�t from an approved source. This keeps your customers� sensitive information�like credit card details�safe from being stolen.
Why It Matters for You
-
Protects Your Customers: CSP reduces the risk of attacks that could harm your customers or damage your reputation.
-
Builds Trust: A secure website reassures customers that their data is safe, encouraging them to shop with confidence.
-
Improves Compliance: CSP helps meet security standards required by regulations like PCI DSS, which is crucial for handling payments securely.
What is Sub-resource Integrity (SRI)?
Sub-resource Integrity (SRI) is another security feature that ensures the external resources your website uses�like scripts, stylesheets, or libraries�are exactly what they�re supposed to be. Many websites, including yours, rely on third-party resources (e.g., JavaScript libraries like jQuery) hosted on external servers. SRI verifies that these resources haven�t been tampered with by hackers.
How SRI Works
SRI uses a cryptographic hash�a unique �fingerprint� of the resource�to verify its integrity. Here�s the process:
-
When we include a third-party resource on your site, we generate a hash of its content and add it to the HTML code.
-
When a customer visits your site, their browser checks the resource�s hash against the expected hash we provided.
-
If the hashes match, the resource loads normally. If they don�t match�indicating the resource has been altered�the browser blocks it.
For instance, if your store uses a page layout script from a third-party provider, SRI ensures that the script hasn�t been modified to include malicious code that could steal customer data or redirect payments.
Why It Matters for You
-
Prevents Tampering: SRI stops hackers from modifying third-party scripts or resources to harm your site or customers.
-
Ensures Reliability: It guarantees that your site functions as intended, avoiding disruptions from corrupted resources.
-
Enhances Security: By verifying external content, SRI adds an extra layer of protection against supply chain attacks, where hackers target third-party providers to compromise your site.
How Volusion Uses CSP and SRI to Protect Your Store
At Volusion, we implement CSP and SRI as part of our broader security strategy to keep your online store safe:
-
We configure CSP to allow only trusted sources for scripts, styles, and other content on your site, minimizing the risk of malicious code execution.
-
We use SRI for all critical third-party resources, ensuring that scripts and libraries your store relies on are authentic and untampered.
These measures work behind the scenes to protect your business and your customers without affecting the functionality or performance of your store. By leveraging CSP and SRI, we help ensure that your website remains a secure and trustworthy place for your customers to shop.
The implementation of CSP and SRI comes due to the new requirements with PCI 4.0. Those are requirements 6.4.3 and 11.6.1.
6.4.3 All payment page scripts that are loaded and executed in the consumer�s browser are managed as follows:�
-
A method is implemented to confirm that each script is authorized.�
-
A method is implemented to assure the integrity of each script.�
-
An inventory of all scripts is maintained with written business or technical justification as to why each is necessary.
11.6.1 A change- and tamper-detection mechanism is deployed as follows:�
-
To alert personnel to unauthorized modification (including indicators of compromise, changes, additions, and deletions) to the security-impacting HTTP headers and the script contents of payment pages as received by the consumer browser.�
-
The mechanism is configured to evaluate the received HTTP headers and payment pages.�
-
The mechanism functions are performed as follows:�
-
� At least weekly OR ��
-
Periodically (at the frequency defined in the entity�s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1).
-
If you have any questions about how we secure your store or want to learn more about our security practices, feel free to reach out to our support team. We�re here to help you succeed safely!
�
How to use Volusion�s CSP Controls
When you turn CSP on, you have to maintain an allow-list of resource types permitted to load from other domain names. For example, let's say you want to load a Facebook/Meta tracking pixel. If you look at the base code, it loads two things: a javascript and an image.
�
The javascript loads from https://connect.facebook.net/en_US/fbevents.js and the image loads from https://www.facebook.com/tr?id=.
First you will go to Settings > Maintenance > Managed 3rd Party Content Security Policy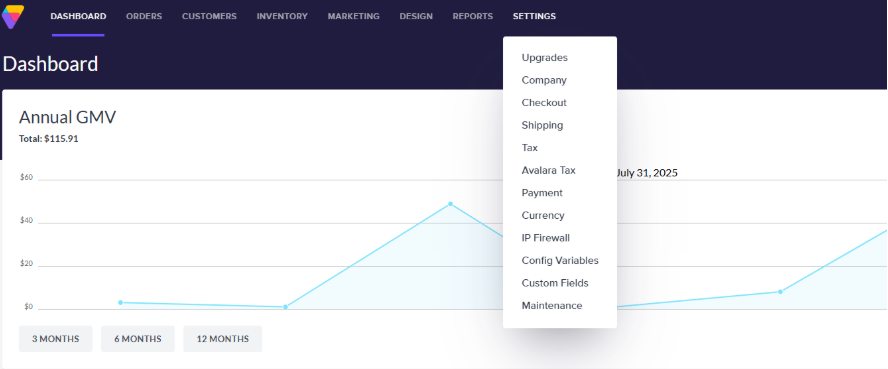 �
�
�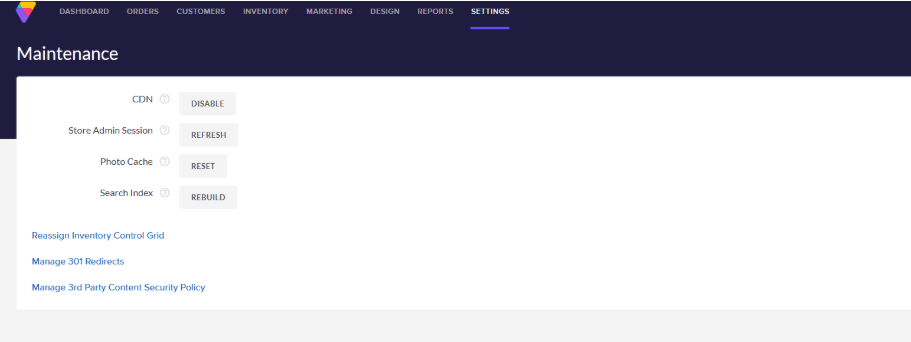 �
�
Click �add� and add the source�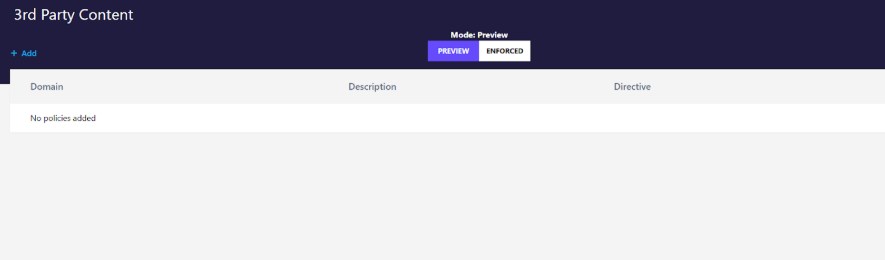 �
�
Leaving the setting set to Preview means it will only warn about insecure content in the console. Selecting Enforced will block any unsecure content from any third party sources.�
You would add the connect.facebook.net domain to the Script Source and the Script Source (Element) resources.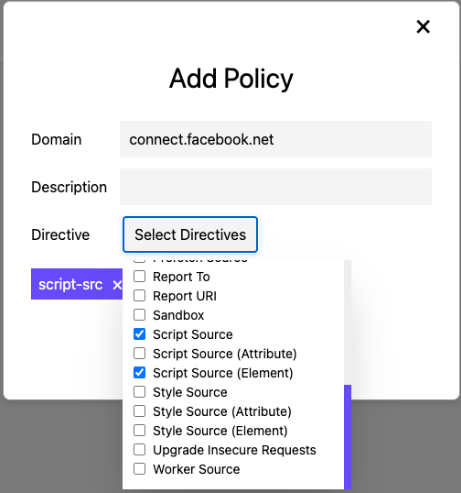 �
�
You would then add the www.facebook.com domain to the Image Source resources.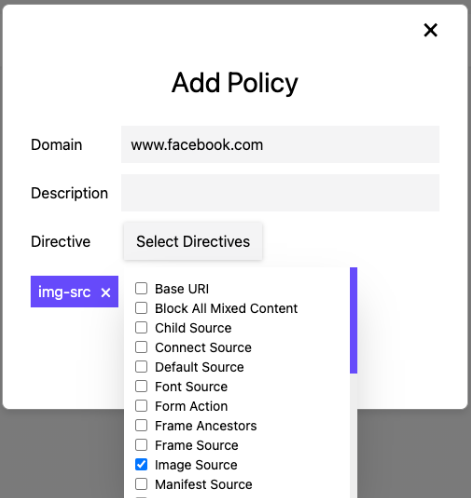 �
�
Every time you load an image, javascript, css file, custom web font, iframe, etc. from a third-party domain that is not the store's domain, it has to have the third-party domain added to the allow-list or else the content security policy will prevent the web browser from loading those resources when the content security policy feature is set to "enforced" mode.
�
If you have third-party resources that you need to load, you will also need to maintain this list if you decide to turn on the enforcement mode for content security policy.
�
If you do not quite understand what CSP is, you can leave/turn it off. However, third-party scanning vendors may decide to fail your PCI scans without the feature enabled.
